According to the Customer Security Controls Framework (CSCF), SWIFT users are required to comply with at least all mandatory controls on an annual basis by undergoing an independent assessment. A SWIFT assessment reviews the security of an organization's SWIFT infrastructure and systems to ensure that they are protected against potential security threats and vulnerabilities.
Last year, with version CSCFv2023, SWIFT published an update of the framework. Tobias Weber, Managing Security Consultant at usd AG and auditor of several international security standards, gives us an insight into the most important changes and the transition phase until the next assessment:

CSCFv2023: Overview of changes
At first glance, it can be noticed that the new version has not introduced any new architecture types. However, some controls have changed in their characteristics. This is due to the following reasons: Hardware Security Modules (HSM) are now mentioned more explicitly in the framework and cloud environments have been included in the framework. Both aspects are reflected in various controls.
In addition, there were specific changes to the following controls:
1.5 Customer Environment Protection
This control was changed from Advisory Control (recommended) to Mandatory Control (mandatory) with the update of the framework. It requires that infrastructure of external environments and potentially compromisable elements should be separated from the general IT environment. Control 1.5 thus has some parallels to Control 1.1, which requires separation of the SWIFT environment from the company's own environment. This is best implemented with suitable firewalls and appropriately maintained firewall rules.
1.3 Virtualization Platform Protection
This control is particularly relevant for organizations that use containers. While it previously only referred to virtualization in the strictest sense, the revised control now requires that containerized applications must also be explicitly considered. Examples of this could be Docker, Kubernetes, or AWS EKS Services.
2.7 Vulnerability Scanning
Control 2.7, which relates to vulnerability scans, has also undergone adjustments: Cloud services have moved into scope and the detection of potential misconfigurations must be covered by the vulnerability scan.
3.1 Physical Security
Control 3.1 for physical security also included an expansion of the scope: Hardware Security Module (HSM) and Cloud Services were included. Interestingly, it is now no longer recommended to disable workstation USB ports. However, from a general security perspective, in workstation operating models where such disabling is possible without major restrictions, my colleagues and I still recommend doing so.
7.3A Penetration Testing
The control requiring regular penetration testing (Pentests) has been weakened. An additional note regulates that not all components have to be tested in every pentest. It is sufficient to test on a risk basis, and results from previous pentests (e.g., a Re-Assessment or sampling) may be used. However, it should be noted that this only applies if there have been no changes to the risk landscape and the IT environment since the last pentest.
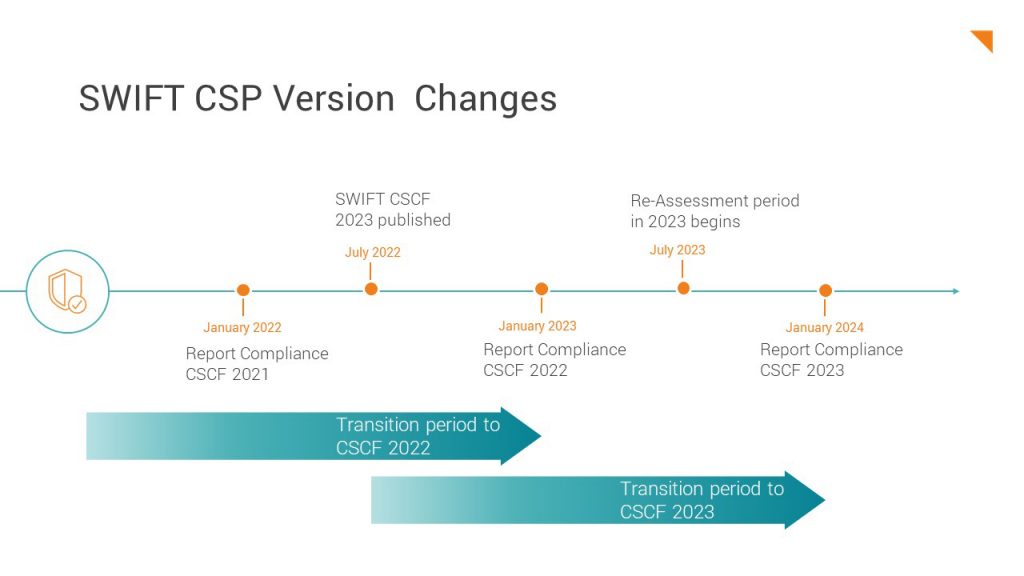
The transition to CSCFv2023
Generally speaking, the phases run at the same intervals: From July of each year until the end of the same year, the corresponding assessments are carried out for all affected SWIFT users, so that they can prove their Report of Compliance in January at the latest.
At the same time, an update of the CSCF for the following year is regularly published in July. The example of 2022 and 2023 shows this well: In July 2022, the CSCFv2023 was presented. At the same time, the Re-Assessment Period 2022 began for all companies, but according to Framework v2022.
In this way, SWIFT not only provides users with a transition period of about one year for the newly introduced frameworks. In addition, the publication of the new framework before the next assessment enables a gap analysis at the same time as the assessment takes place: To what extent are there changes in the newly published controls and which implementations are necessary until the next assessment in order to fulfill them? In order to be well prepared, SWIFT users should deal with the changes early on.
Outlook
Compliance is a continuous process, not a one-time project. Many of you are now in the midst of implementing compliance measures and processes with CSCFv2023. The Re-Assessment phase will start in July 2023.
At the same time, a new version of the CSP is expected mid-year. SWIFT has indicated that in this update, Controls 2.4 (Back Office Data Flow Security) and 2.8A (Critical Activity Outsourcing) may become Mandatory Controls.
In the previous blog post, we covered how the redefined Re-Assessment process fits into the existing SWIFT CSP assessment process and what benefits it can bring to SWIFT users.
Do you have questions or need assistance with your upcoming SWIFT assessment? Contact us, we're happy to help.



