“Promptly”, “quarterly”, “periodically”: Many PCI DSS requirements demand that measures be implemented within a specified timeframe. While version v3.2.1 of the PCI DSS left some room for interpretation here, version v4.0 contains specific explanations for the first time. This way, the Payment Card Industry Security Standards Council (PCI SSC) aims to prevent discussions and disagreements between organizations, their assessors and credit card organizations.
But what exactly does “periodically” mean? What happens if your company exceeds a specified timeframe? And what do you need to consider in your first PCI DSS assessment? Find answers to these questions in this article.
Timeframes in PCI DSS v4.0
The Council requires that activities are carried out at intervals that are as close as possible to the specified time frame without exceeding it. It only sets minimum requirements - you are of course free to carry out measures more frequently if necessary.
Here is a complete overview of the new timeframes defined in PCI DSS v4.0:
| Immediately | Without delay. In real time or near real time. |
| Promptly | As soon as reasonably possible. |
| Daily | Every day of the year (not only on business days). |
| Weekly | At least once every seven days. |
| Monthly | At least once every 30 to 31 days, or on the nth day of the month. |
| Every three months (“quarterly”) | At least once every 90 to 92 days, or on the nth day of each third month. |
| Every six months | At least once every 180 to 184 days, or on the nth day of each sixth month. |
| Every 12 months (“annually”) | At least once every 365 (or 366 for leap years) days or on the same date every year. |
| Periodically | Frequency of occurrence is at the organization's discretion and is documented and supported by the organization’s risk analysis. The organization must demonstrate that the frequency is appropriate for the activity to be effective and to meet the intent of the requirement. |
| Significant change | Certain requirements relate to significant changes to a company's environment. Exactly what constitutes a significant change depends heavily on the company and its environment. Specific activities have a potential impact on the security of the CDE (Cardholder Data Environment). At least the following activities are to be assessed as significant changes: - New hardware, software, or networking equipment added to the CDE. - Any replacement or major upgrades of hardware and software in the CDE. - Any changes in the flow or storage of account data. - Any changes to the boundary of the CDE and/or to the scope of the PCI DSS assessment. - Any changes to the underlying supporting infrastructure of the CDE (including, but not limited to, changes to directory services, time servers, logging, and monitoring). - Any changes to third party vendors/service providers (or services provided) that support the CDE or meet PCI DSS requirements on behalf of the entity |
A major change: You can define “periodically" at your discretion
Where the PCI DSS does not define a minimum frequency, periodic fulfillment of certain requirements is permitted. The reason for this flexibility is the new, more risk-based approach to PCI compliance. You determine the frequency of periodic activities in your organization, depending on the risk, the business, and the processes. Your organization's security policy and a targeted risk analysis in accordance with PCI DSS Requirement 12.3.1 will help you to determine an appropriate frequency. You must demonstrate that it is sufficient to fulfill the purpose of the requirements.
What happens if my organization exceeds the deadline for a specified activity?
Generally, your organization should implement a documented process not only for activities that are performed at specific points in time but also for activities that are performed periodically. This process includes at least the following steps:
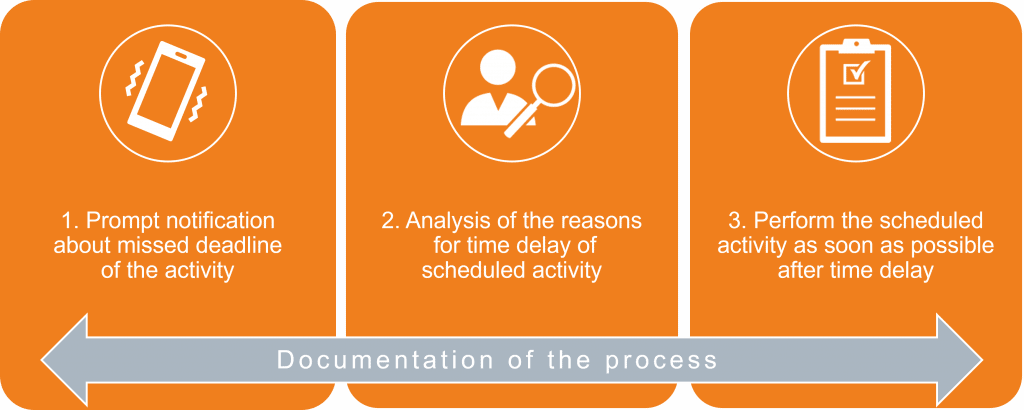
If you have established this process and follow its steps if you should ever exceed the deadline for an activity, your “compliant” status does not automatically expire.
However, if no such process is in place and/or the activity was not performed as planned due to oversight, mismanagement or lack of monitoring, you have not met the relevant requirement. In such a case, you can still comply with the requirement if your organization
- documents or reconfirms the previously described process to ensure that the planned activity is performed on time,
- redefines the schedule,
- provides evidence that the planned action has been performed at least once according to its schedule.
Timeframe for an organization's initial PCI DSS assessment
If you are certified for the first time according to PCI DSS, you do not have to demonstrate that you have already performed activities for each specified timeframe in the previous year. Your PCI assessors will want to validate only the following aspects:
- The activity was performed in compliance with the requirements within the last timeframe (e.g. the last three-month or six-month period)
- Your organization has documented policies and procedures for the continuing implementation of the activity within the defined timeframe
For subsequent years after the first assessment, the activity must have been performed at least once within each required timeframe.
Is your first PCI DSS v4.0 assessment coming up?
In our free usd webinar on Targeted Risk Analysis, our colleague Tobias Weber will take you on a deep dive into the topic. You can rewatch the webinar here.
For more information about PCI DSS v4.0, check out our blog posts and webinar recordings. Do you have further questions? Do not hesitate to contact us.




