News
PCI DSS v4.0.1: Are You Ready for the Future-dated Requirements?
With the publication of PCI DSS v4.0.1, at the latest, the requirements introduced with version 4.0 of the credit card data security standard are...
Information Security in the Financial Sector: How Frankfurter Sparkasse is Tackling the Mammoth Task
The digital transformation in the financial sector has created new areas of attack for cyber criminals and therefore significant risks for...
Security Advisory on AXIS Webcam
The pentest professionals at usd HeroLab examined the AXIS Webcam (P1364) during their pentests. Our professionals discovered a vulnerability...
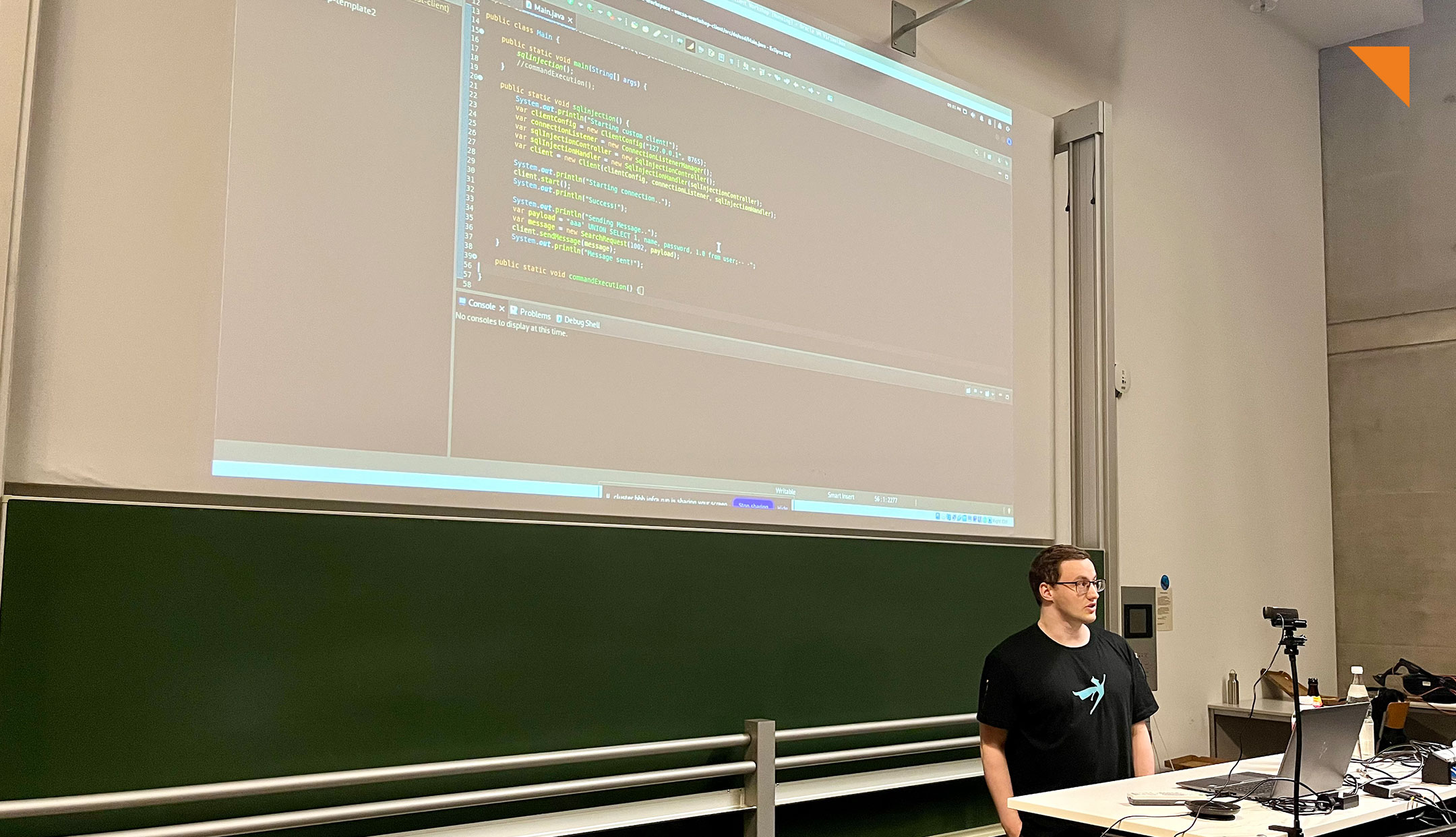
Fat Client Pentesting: Hands-On Decompilation & Exploitation - Guest Lecture at Hochschule München University of Applied Sciences
Last Tuesday, usd visited the Hochschule München University of Applied Sciences for the second time as part of the "IT Security" lecture series. Our...
Targeted Risk Analysis - PCI DSS introduces Individual Risk Assessment Tool
With the introduction of PCI DSS v4.0, many requirements and processes have changed significantly. Some of the new requirements are future-dated...
Top 3 Vulnerabilities in SAP Pentests
During their penetration tests (pentests), our security analysts at usd HeroLab repeatedly uncover vulnerabilities that pose significant risks to...
Hacker Contest Challenge of Summer Semester 2024: Sample Solution online
This summer semester, the "Hacker Contest" will be taking place again at the Technical University (TU) Darmstadt and Darmstadt University of Applied...
PCI DSS v4.0.1 Released
In response to stakeholder feedback and questions received since the release of PCI DSS v4.0 in March 2022, the PCI Security Standards Council (PCI...
NIS-2: The Most Important Takeaways from the German Implementation Act
The law implementing the NIS-2 Directive aims to transpose the requirements of the European NIS-2 Directive into the German legal system. On May 7,...
Security Advisory on WeKan
The pentest professionals at usd HeroLab examined the open source application WeKan during their pentests. This application offers users a solution...
Top 3 Vulnerabilities in Fat Client Pentests
During their penetration tests (pentests), our security analysts at usd HeroLab repeatedly uncover vulnerabilities that pose significant risks to...
DORA Deep Dive: Threat-Led Penetration Testing (TLPT)
The Digital Operational Resilience Act (DORA) will apply as of January 17, 2025. In addition to routine operational resilience testing, DORA will...