During penetration tests our security analysts repeatedly uncover gateways in IT systems and applications that pose significant risks to corporate security. They increasingly identify the same vulnerabilities in different IT assets, some of which have been known for years. In our mini-series, we present our top 5 most notable vulnerabilities from 2020. Part 3: SQL Injection
Vulnerability Background
SQL injection vulnerabilities allow an attacker to inject own database commands into legitimate database queries. This can be used for various types of attacks. Usually, a successful attack allows full access to the application-relevant parts of the database. In many cases, it is then possible to escalate permissions within the database or to access the server‘s file system. In the worst case, an SQL injection vulnerability allows the execution of arbitrary operating system commands on the underlying server.
Exemplary hacker attack and its consequences
The following example demonstrates an SQL injection vulnerability that ultimately allows the attacker to access password hashes of registered users. The initial entry point is located inside a search function for forum posts.

The screenshot above shows the vulnerable search function, that can be used to search forum posts by title. Inserting special characters within the search query can provoke a database error, as demonstrated in the following screenshot:

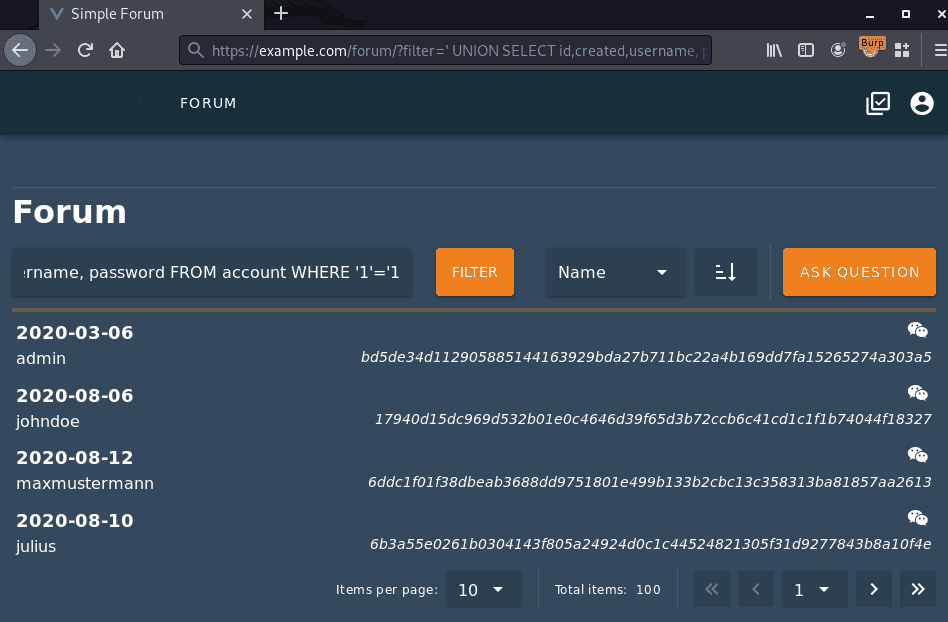
Based on the obtained database error, an attacker can now refine the attack. The following screenshot shows how the vulnerability can be exploited to extract password hashes from the database:
Recommended measures
User-controlled input should always be considered potentially dangerous and should never be used within database queries without sufficient filtering and encoding. Appropriate functions for filtering input are available in all common programming languages. Furthermore, it is recommended to use prepared statements. With this technique, the structure of a database query is sent to the database server in advance, before the data actually used for the query is inserted. The database server thus knows the structure of the query and subsequent modification by an attacker is no longer possible.
Please note that this is a very general recommendation for security measures. We are happy to support you with individual solutions. Feel free to contact us.

Read more about our top 5 most notable vulnerabilities and other exciting topics in our 2020 Annual Report.



