In this short series we provide you with useful facts about the Payment Card Industry Data Security Standard. Be well informed on your PCI DSS certification.
What is the PCI DSS scope?
The scope of a PCI DSS certification includes all components of a company’s environment that must meet the PCI DSS control objectives. In its “Scoping Guidance“, the PCI Security Standards Council (PCI SSC) sets out the PCI SSC’s definition of scoping.
First, the Council defines the “CDE” (Cardholder Data Environment): The CDE consists of all persons, processes and technologies that store, process or transmit cardholder data or sensitive authentication data.
The PCI DSS scope includes all system components that are located in or connected to the CDE and those systems that could have an impact on the security of the CDE.
An organization is responsible for correctly defining its own PCI DSS scope. An accredited Qualified Security Assessor will verify the correct scope before the PCI DSS assessment itself takes place. It is recommended that companies seeking a PCI DSS certification document all systems that store, process and transmit card data.
What are connected-to systems and systems with security impact?
Connected-to systems or systems with a security impact on the CDE are all systems that:
- are located on other networks, but have a connection to or access to the CDE
- connect or have access to the CDE via third party systems (e.g. Jump Server)
- influence the configuration or security of the CDE, or influence how card data is processed (e.g. workstations of administrators)
- provide services to secure the CDE (e.g. firewalls)
- provide services to meet PCI DSS requirements (e.g. log servers)
- serve to segment the CDE from other networks (e.g. switches)
The connection can be physical (Ethernet, Powerline, USB etc.), wireless (WLANs, GPRS, Bluetooth, mobile radio etc.) or virtual (virtual networks, virtual machines, virtual firewalls, virtual switches etc.).
What systems are not in scope?
Only systems that
- do not store, process or transmit card data and
- re not on the same network as the CDE, and
- have no connection or access to systems in the CDE, and
- have access neither to the CDE nor to other systems that are in scope and have no influence on the security of the CDE, and
- do not meet any of the above criteria for connected-to systems or systems with a security impact
can be excluded from the scope of a PCI DSS assessment.
How can I reduce my organization’s scope?
The PCI DSS Scope can be reduced by organizational and technical measures:
- System & Application Level – Check whether the card data is needed on all systems/applications.
- Network level – Check whether all systems muste be run on the same network.
- Logical – Minimize access rights to card data.
- Physical – Limit IT systems with card data to only one location.
What is network segmentation?
Although it is not a direct requirement of the PCI DSS, appropriate network segmentation can significantly reduce the scope of the CDE and thus the scope of the PCI DSS assessment. Network segmentation, also known as “segmentation” or “isolation”, isolates system components that store, process or transmit card data from systems that do not. Without network segmentation (“flat network”), the PCI DSS requirements must be met for the entire network and all connected IT systems.
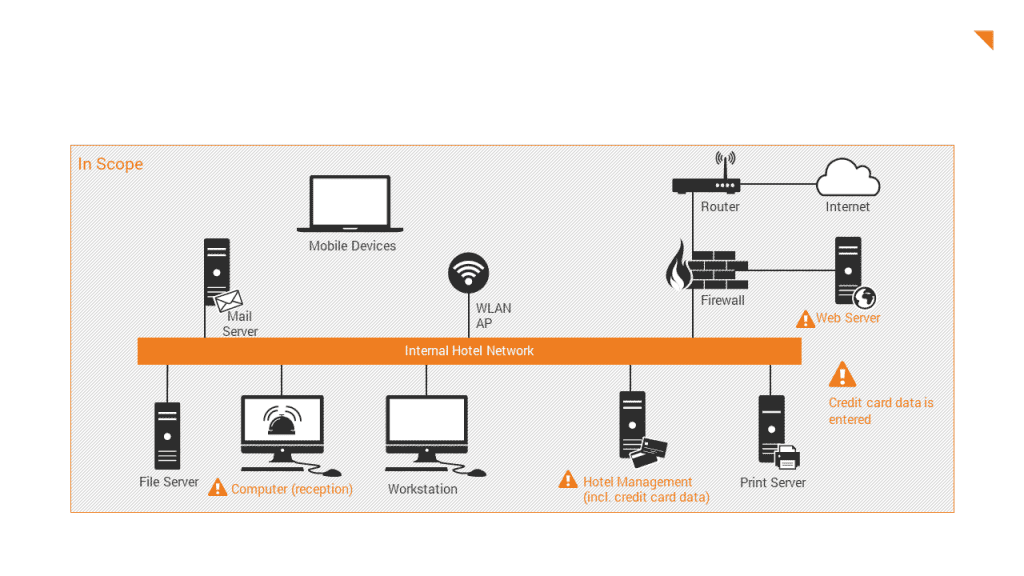
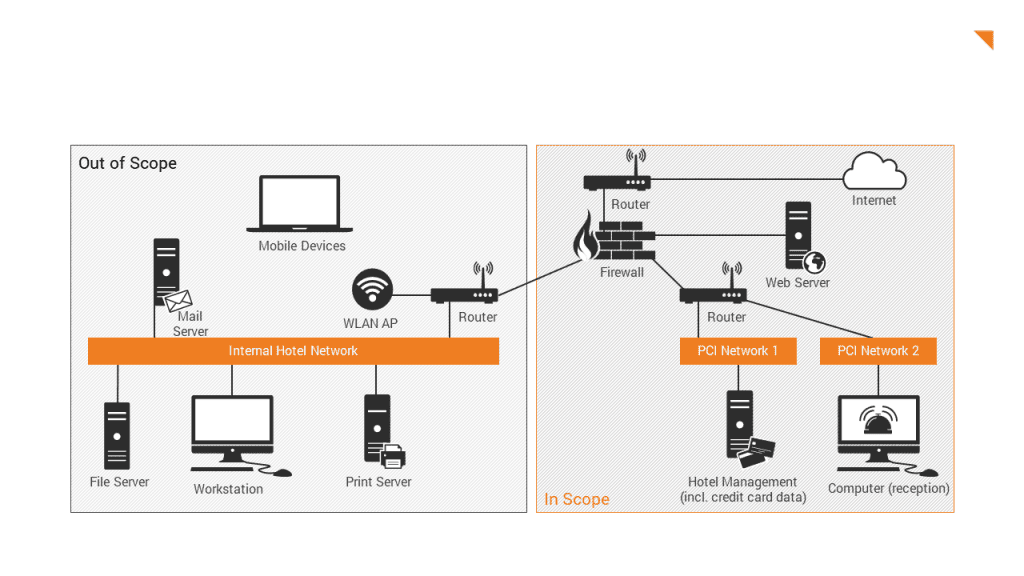
What are the consequences of incorrect scoping?
Inappropriate scoping can result in major problems for any organization. If the scope is identified incorrectly so that it includes more components than it needs to, not only the assessment itself, but also potential corrective actions will be more complex and cost-intensive than necessary. If the scope is defined too narrowly, on the other hand, it may exclude people, processes, systems or networks that could impact the security of the CDE and cardholder data or sensitive authentication data may be underprotected. It is therefore important that companies identify and verify their PCI DSS Scope with due diligence. Professional advice from qualified PCI experts can be enormously helpful in this regard.
Do you have any questions or need assistance in identifying or reducing your PCI DSS Scope? Contact us, we are happy to help.



