Last updated: 30 July, 2024
The Digital Operational Resilience Act (DORA) aims to strengthen digital resilience in the European financial sector. To this end, the EU regulation formulates corresponding requirements for affected financial institutions and their third-party ICT service providers in 45 articles. The challenge for these companies is now to derive specific implementation measures for their company from the requirements of the regulation.
The European Supervisory Authorities (ESAs) are therefore publishing supplementary standards and guidelines alongside the regulation itself, which contain binding requirements and guidance on implementation. This was also the case on July 17, 2024: less than six months before DORA applies, the ESAs published a second batch of RTS, ITS and other guidelines. The batch focuses on threat-led penetration testing and the reporting framework for ICT-related incidents.
What is the purpose of RTS & ITS?
Nowadays, it is increasingly important for financial companies to manage the risks of digitalization and the associated high dependency on information and communication technology (ICT) through a suitable organizational structure and an effective internal control system (ICS). The Regulatory Technical Standards (RTS) and the Implementing Technical Standards (ITS) play a decisive role in this: they provide affected companies with concrete assistance in implementing the requirements and provisions of the DORA Regulation.
The European Supervisory Authorities (ESAs), consisting of
- the European Banking Authority (EBA),
- the European Securities and Markets Authority (ESMA),
- and the European Insurance and Occupational Pensions Authority (EIOPA)
are responsible for the elaboration of the two standards.
Regulatory Technical Standards (RTS)
The RTS are binding technical standards. They specify the requirements set out in DORA and define how these are to be implemented in practice. When it comes to reporting serious ICT-related incidents, for example, the RTS contains a list of specific content for the initial report and specifies the interim and final reports to the supervisory authority.
Implementing Technical Standards (ITS)
The ITS supplement the RTS by specifying detailed implementation instructions and necessary processes to fulfill the requirements of the RTS. Just like the RTS, compliance with the ITS is mandatory. Using the example of reporting serious ICT-related incidents, the ITS contains a list of supplementary information to the reporting templates.
Which RTS and ITS have been released so far?
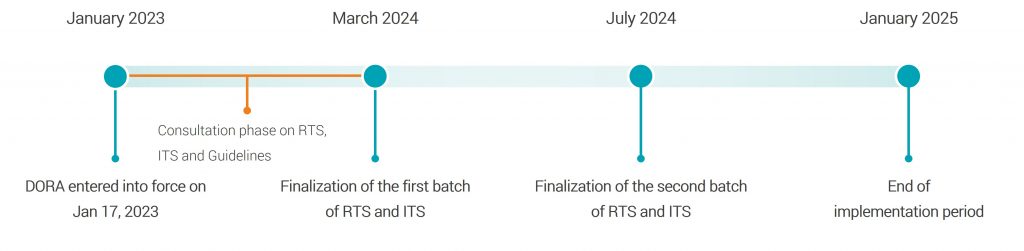
In the first publication round in March 2024, the following standards were published for clarification:
- RTS on ICT risk management (Art. 15, Art. 16. para. 3)
- RTS on the classification of ICT-related incidents (Art. 18.3)
- RTS on contractual agreements with third-party ICT service providers (Art. 28.10)
- ITS on the information register (Art. 28.9)
The following standards were added on July 17, 2024:
- RTS on the reporting of major ICT-related incidents and significant cyber threats (Art. 20a)
- ITS on the reporting of major ICT-related incidents and significant cyber threats (Art. 20b)
- RTS on threat-led penetration testing (Art. 26.11)
- RTS on the harmonisation of conditions enabling the conduct of the oversight activities (Art. 41.1)
- RTS specifying the criteria for determining the composition of the joint examination team (JET) (Art. 41.1c)
The following standard from the second batch was subsequently published on July 26, 2024:
- RTS on subcontracting ICT services supporting critical or important functions (Art. 30.5)
"There are still many question marks surrounding specific interpretations of DORA - the RTS and ITS will help resolve these. From our point of view, two of the standards are particularly interesting: firstly, the RTS on ICT risk management, as it provides us with clarity on the ICT risk management framework, including the guidelines for ICT security and ICT-related incidents, as well as the management of ICT business continuity. And secondly, the ITS for creating an information register is becoming increasingly important. Because BaFin has stated that it will begin evaluating reported information registers as early as the beginning of 2025."
Simon Weickart, Managing Security Consultant, usd AG

Do you need support?
We are here for you if you need support in analyzing or implementing the DORA requirements in your company. Feel free to contact us at any time.



