During penetration tests our security analysts repeatedly uncover gateways in IT systems and applications that pose significant risks to corporate security. They increasingly identify the same vulnerabilities in different IT assets, some of which have been known for years. In our mini-series, we present our top 5 most notable vulnerabilities from 2020. Part 1: Cross-site scripting
Vulnerability Background
Cross-site scripting refers to a category of vulnerabilities that allow an attacker to inject malicious JavaScript code into a web server‘s responses. The web browser of other users then cannot distinguish the JavaScript code inserted by the attacker from the legitimate code of the application and executes malicious scripts accordingly. This usually leads to the attacker being able to completely take over the victim‘s current session.
Exemplary hacker attack and its consequences
The HTTP request below shows how an attacker embeds malicious JavaScript code within an application. Now, when a victim visits the corresponding endpoint within the application, the JavaScript code is executed in his browser context. The JavaScript used in this example extracts the victim’s credentials, which were stored within the browser:
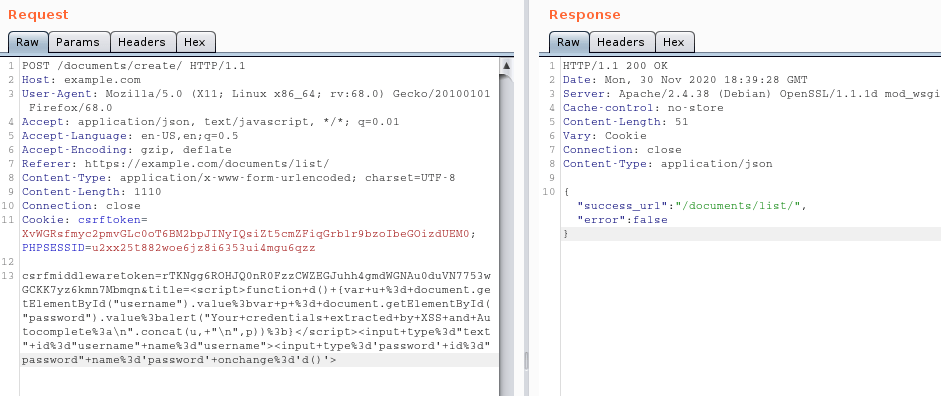
Figure 1: Attacker places malicious JavaScript code inside a vulnerable application
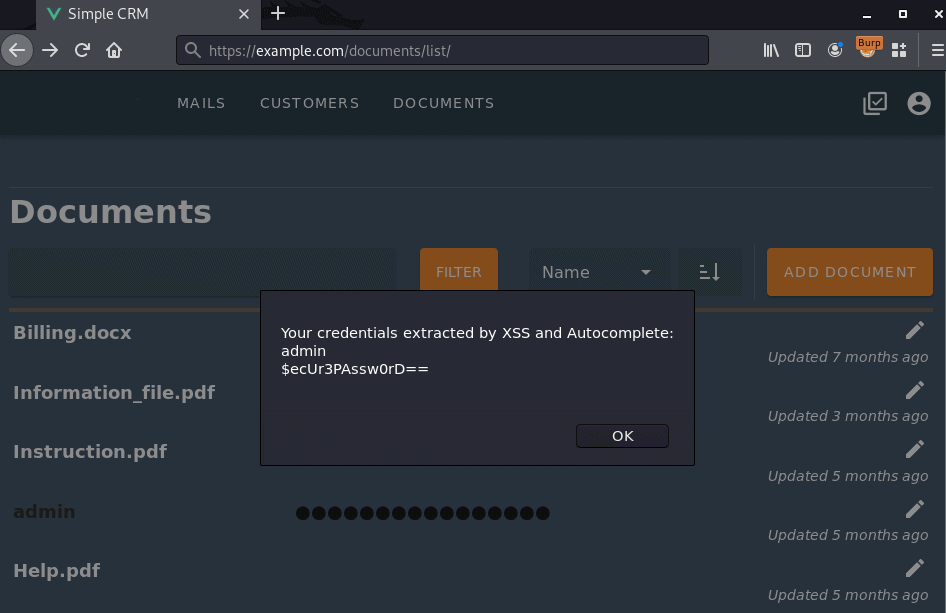
Figure 2: A user visits the vulnerable page – their credentials are extracted
While the victim‘s credentials were displayed here for better visibility, a real attack would take place without any traces visible to the victim. Instead of being displayed on screen, the accessed data would have been sent over the network to a server controlled by the attacker.
Recommended measures
User-controlled input should always be considered potentially dangerous and should never be embedded within server responses without sufficient filtering and encoding. Appropriate functions for filtering and encoding input are available in all common programming languages. The correct use of frameworks and regular training of developers are important measures to prevent cross-site scripting vulnerabilities.
Please note that this is a very general recommendation for security measures. We are happy to support you with individual solutions. Feel free to contact us.



