During their penetration tests (pentests), our security analysts at usd HeroLab repeatedly uncover vulnerabilities that pose significant risks to corporate security. They increasingly encounter the same vulnerabilities. Our blog series "Top 3 Vulnerabilities" presents them and provides tips on how to avoid them - for #moresecurity across all IT assets.
Today we look at the three most common security-critical vulnerabilities that our analysts have identified in Active Directory Pentests in recent years.
Why Active Directory Pentests?
Windows Active Directory (AD) is still the backbone of identity management in most corporate environments. It facilitates the management of users, devices and their respective authorizations. This feature makes AD a prime target for attackers who try to exploit its intricacies to gain unauthorized access. This allows attackers to steal or manipulate business-critical data and take control of the most sensitive business processes.
Misuse of the Access Control List
One focus of Active Directory Pentests (AD Pentests) is the investigation of vulnerabilities in the Access Control Lists (ACL). In general, ACLs regulate the access rights of users and groups to network resources. However, ACLs are often improperly configured or too permissive. This unintentionally rolls out the red carpet to attackers. They exploit the vulnerability to extend their privileges, move laterally in the network or establish themselves permanently. This can undermine the integrity and confidentiality of sensitive data.
And how exactly does this attack work? The attackers abuse the so-called writeDACL authorizations. This involves changing the DACLs (Discretionary Access Control List) of AD objects and the attackers grant themselves higher privileges. It is not necessary for them to be directly included in privileged groups. This manipulation of overly extensive authorizations also allows attackers to change AD attributes or group memberships. This paves the way for further attacks in the corporate environment.
Security tip:
Performing regular AD configuration assessments and implementing the principle of least privilege can mitigate vulnerabilities. In addition, sophisticated monitoring tools can be used to detect suspicious activities that indicate ACL tampering at an early stage.
Active Directory Certificate Services
Active Directory Certificate Services (ADCS) is an important component in many AD environments for the creation and management of certificates within an organization. It is important for organizations to ensure that ADCS are resilient to vulnerabilities as these services are widely used and help secure environments.
For example, the white paper "Certified Pre-Owned" illustrates the complexity of ADCS vulnerabilities. It shows how attackers can manipulate certificate processes in order to obtain certificates with higher privileges. Consequently, this manipulation allows them to extend their access within a network. Since the publication of the white paper, many different variants of ADCS vulnerabilities have been found. These vulnerabilities are usually referred to as an extension of the original whitepaper and follow the naming convention ESC1 to ESC14, with ESC14 being the most recently discovered vulnerability.
A configuration error can be described as the core of the ESC1 vulnerability. Attackers can use this error to extend their authorizations. This vulnerability originates in the way certificate templates are managed and processed. The attackers exploit this by manipulating certificate requests to obtain certificates that grant them higher privileges.
Imagine the scenario like this: An attacker requests a certificate with simple user credentials. This is based on a template that is not properly configured. This enables client authentication. If this is successfully exploited, the attacker could impersonate another user or even an administrator and gain unrestricted access to sensitive areas of the network.
Security tip:
Implementing strict access controls and monitoring certificate issuance helps to prevent unauthorized access and certificate tampering. Improving the transparency of certificate operations is also crucial. Companies should implement comprehensive logging and auditing mechanisms to track the issuance and revocation of certificates. In this way, suspicious activities that could indicate an attack can be detected in good time and measures can be initiated accordingly.
Relay Attacks
Mechanisms such as NTLM (NT LAN Manager) and Kerberos in particular make authentication easier. However, these mechanisms are very vulnerable to attack techniques such as relaying. A vulnerability can lead to unauthorized access and possibly to the complete compromise of the domain. Understanding possible attack scenarios and mitigating NTLM and Kerberos relaying attacks helps to strengthen network defenses.
In NTLM relaying attacks, authentication requests are intercepted by a client and forwarded to another server in the network. This allows attackers to impersonate a legitimate user without having to crack or steal the user's credentials. Attackers exploit the lack of mutual authentication of the NTLM authentication protocol. Attackers extend their privileges within a network in order to access sensitive information. In the worst-case scenario, they could take control of the domain controller, which poses a significant threat to network security.
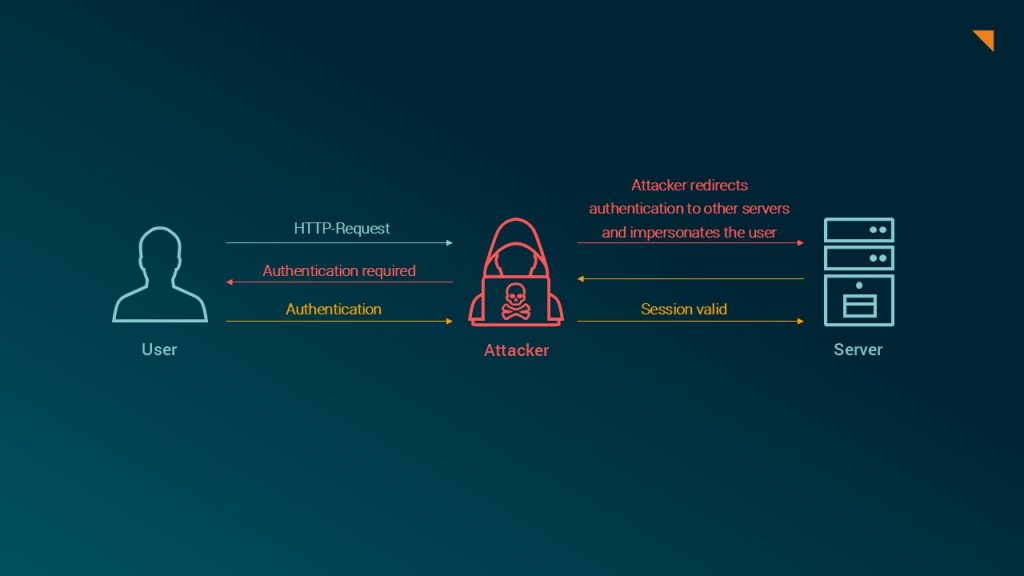
In contrast, Kerberos is equipped with a service-specific authentication ticket to prevent relaying. Nevertheless, attackers can manipulate this mechanism under certain conditions. This vulnerability arises from the possibility of abusing the Service Principal Names (SPNs). This allows unauthorized access to services if attackers can control or predict the SPNs. Effective mitigation of this vulnerability requires a robust service configuration and vigilant monitoring of authentication practices. This underscores the need for companies to understand and protect their Kerberos implementations against such sophisticated attacks.
Security tip:
Mitigating the risks associated with relaying attacks requires a comprehensive and proactive approach. An important strategy is to disable NTLM authentication where possible and favor more secure protocols such as Kerberos due to the inherent vulnerabilities of NTLM. Enabling SMB signing also plays a crucial role. It helps to prevent NTLM relaying by ensuring that SMB packets are authenticated and not modified. In addition, the configuration of LDAP signing and LDAP channel binding can prevent the forwarding of LDAP authentication attempts and thus protect against unauthorized access to directory services.
Let's Sum It Up
Protecting Active Directory in the context of corporate cybersecurity is critical. Addressing vulnerabilities such as ACL abuse, ADCS misconfigurations and NTLM and Kerberos relaying attacks is essential to maintaining a robust network defense.
Our Active Directory penetration tests (AD Pentest) are specifically designed to uncover and mitigate these and other vulnerabilities. They provide the necessary expertise and proactive measures to improve security and resilience against evolving cyber threats. Contact us, we will be happy to help you.



