Cyber Security Check
Test your processes, technology & security awareness
The cyber threat level was as high as ever in the past year (source: BSI). The financial and reputational damage was enormous. How well are you protected against cyber attacks?
Strong cyber security despite digitization
Driven by digitalization, you process, store and transmit a large amounts of sensitive information on a daily basis via a wide variety of IT systems and applications. At the same time, the complexity of employed security processes and tools increases. Therefore, it is becoming increasingly challenging to keep track of your security posture. Nevertheless, your customers trust you with efficiently protecting their datat against cyber-attacks.
How well do you know your own security posture?

We recommend conducting a Cyber Security Check whenever there is no or insufficient clarity about your security level and the associated risks. Additionally, we suggest performing the Check during crucial phases of your business, such as after a management change or in the context of an audit.
Protect your data with a Cyber Security Check
Based on internationally recognized information security standards, the recommendations of ISACA, ISC², ISF and the German Federal Office for Information Security, as well as current best practices, our security auditors conduct a Cyber Security Check at your premises. We thoroughly examine your processes and technology as well as the security awareness of your employees.
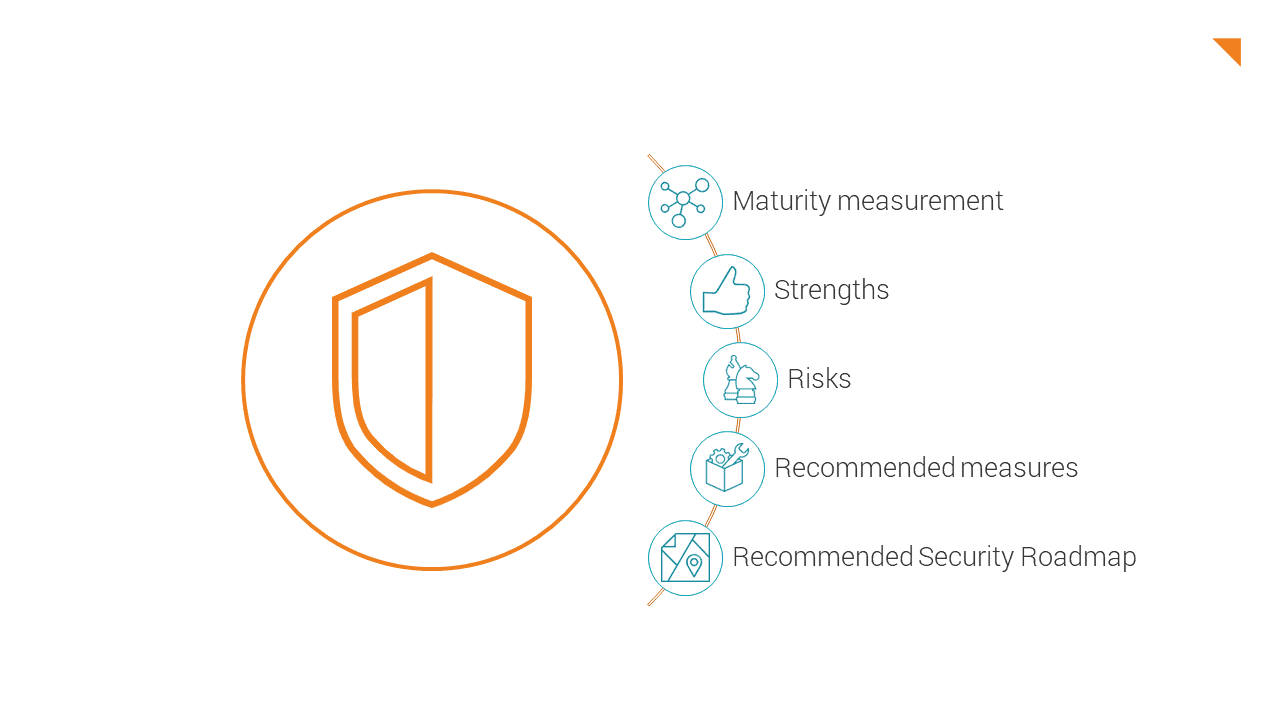
How do we proceed when performing a Cyber Security Check?
We tailor each Cyber Security Check to your needs and circumstances. The results regarding your security level are presented in the manner and depth you desire. Typically, the Cyber Security Check consists of a planning phase, the execution of the Check and the presentation of the results.
What will be checked during a Cyber Security Check?
Our security auditors use the CSC Control Framework developed by usd as the basis for our Cyber Security Check. The Control Framework covers the four essential areas of your cyber security and includes up to 240 individual requirements:
- Governance (e.g. Asset Management, Service Provider Management)
- Prevention (e.g. Security Trainings, Cloud Security)
- Detection (e.g. Audit Log Management, Security Event Management)
- Response & Recovery (e.g. Incident Management, Business Continuity)
Optional consulting services:
- Consulting on the implementation of recommended measures
- Preparation of a detailed final report
- Conducting follow-up assessments after implementing recommended measures
- Annual Cyber Security Check to track security level changes and ensure a consistently high security level